What to do if someone crashes your Zoom meeting
Learn about the Zoom settings that help you respond to gatecrashers.
Zoom bombing is an unwanted person joining your meeting, eavesdropping or causing mischief, like posting obnoxious material to the screen or in the chat. It can occur if the meeting link was forwarded to others or posted on social media or a public website, and if your Zoom security settings are inadequate.
Zoom includes features to make your meeting secure but first we’ll talk about what to do if you are caught out.
What can you do during a Zoom bombing incident?
Meeting hosts and co-hosts have the ability to take the following action.
Suspend participant activities
Stop all users from chatting, sharing their screen, using the whiteboard etc. It will also lock the meeting so that new users cannot join. This is available from the meeting Security button on the Zoom toolbar. You will be given the option to report the incident to Zoom support – they may be able to assist in further investigation and take appropriate action.
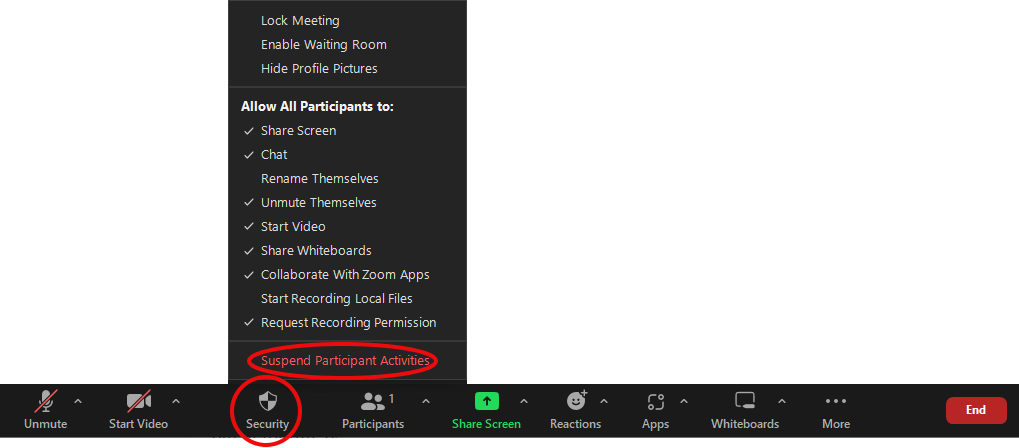
Zoom toolbar with the security icon highlighted. The security option to Suspend participant activity is circled.
Remove the user
Rather than fumbling around in Zoom, trying to take down the unwanted material, find the unwanted user and remove them.
- From Zoom, open the Participants panel.
- Look for the user’s name (or screen name).
- Click the three dots next to their name and choose ‘Remove’.
As the meeting is now locked, they will be unable to re-join your meeting.
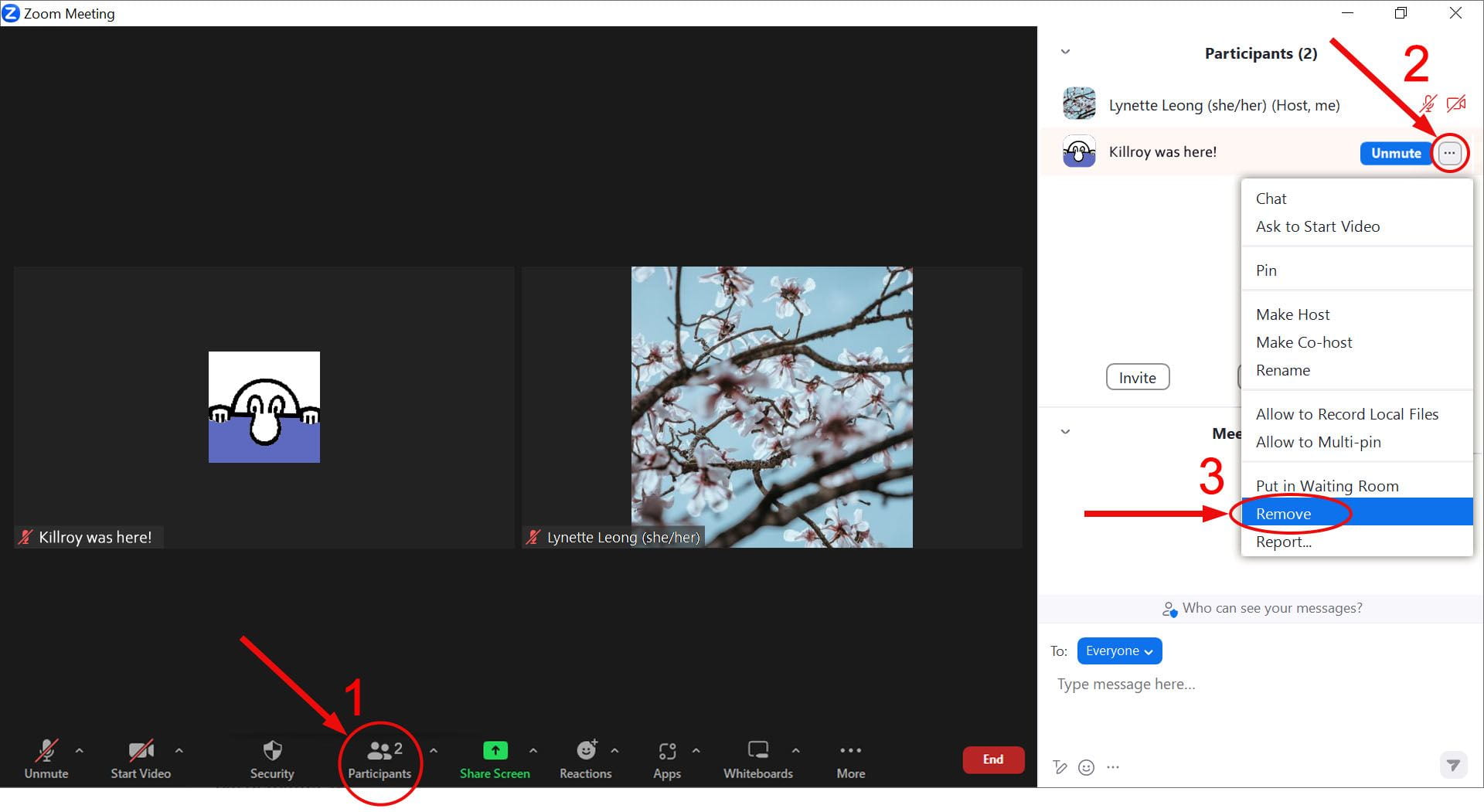
Zoom toolbar with participants icon highlighted. A panel showing all meeting participants is displayed with a remove user option next to someone’s name.
Resume the meeting
Once you have controlled the situation and the miscreant has gone, re-enable the security measures that you are comfortable with, like Enable participants to: Chat, Unmute themselves, and Start video.

Zoom toolbar with the Security icon highlighted. Participants security settings that are enabled are: chat, unmute themselves, and start video.
At this point, screen sharing will be disabled for everyone except hosts and co-hosts. If you have a guest presenter wanting to share their screen, make them a co-host by clicking the three dots next to their name in the Participants panel.
See also
Schedule secure meetings
In advance of the meeting, make sure your Zoom settings restrict the likelihood of unwanted visitors.
Zoom video conferencing
All the other stuff relating to Zoom.
Page updated 10/04/2025 (page added)
