Schedule secure meetings in Zoom
In advance of the meeting, make sure your Zoom settings restrict the likelihood of unwanted visitors.
Note: We recommend using using the web browser version of the Zoom scheduler rather than the App version, especially if your meeting will have external presenters/guests. A setting to allow exceptions for externals is missing from the App.
Scenario one: Your Zoom meeting is for UoA participants and (optionally) known external presenters/guests
Follow these steps if your meeting is for UoA staff and/or students and known externals.
![]()
Avoid using your Personal Meeting ID (PMI) for links to advertised/public meetings. Generate a unique meeting ID for each session or recurring series of meetings.
Make sure that Passcode remains ticked; this adds a layer of security.
Select Require authentication to join then select University of Auckland from the dropdown menu. Users who are not signed into Zoom with their University credentials (or granted an authentication exception) will be unable to join.
Alternative hosts / co-hosts
If you know in advance who will be co-presenting with you (to enable screen-sharing etc.) make them an alternative host. Click Show for Advanced options.
Type their name into the Alternative Hosts field to select your colleague. You cannot add externals from here but you can add them as alternative hosts once the meeting has started by clicking the three dots next to their name in the Participants panel.
Scenario two: If your Zoom meeting is open to external participants, use a Waiting Room to control access
Follow these steps when you expect external participants and when it is not practical to arrange authentication exceptions for them in advance.
When scheduling the meeting, select Require authentication to join then select Sign in to Zoom from the dropdown menu. Users who are not signed into Zoom will be unable to join.
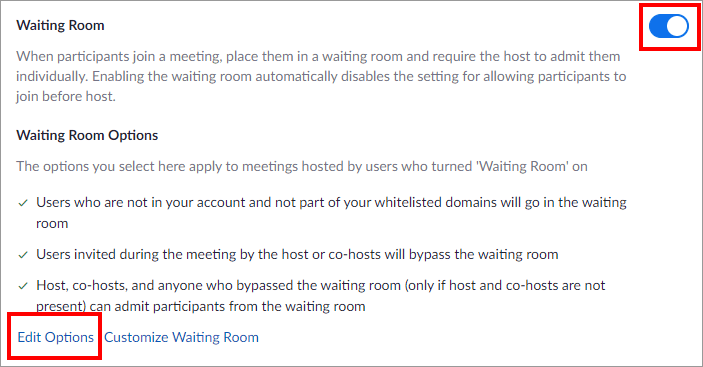
Enable the Waiting Room. This allows you to vet external participants before granting them access. The Waiting Room requires a host or co-host to let people join a meeting in progress via the Participants panel. Although participants can choose any ‘screen name’ they like, this step reduces the likelihood of undesirables ‘bombing’ your meeting; you can let people in who you recognise.
Set up your alternative hosts as usual (see the instruction for scenario one).
If during the meeting you want an external participant to screen-share, you can assign them as an alternative host by clicking the three dots next to their name in the Participants panel.
Allow UoA participants to bypass the Waiting Room
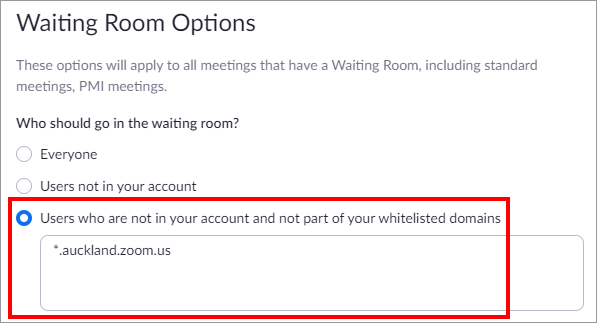
Add a trusted domain to reduce the number of people that you have to manage via the Waiting Room. For University of Auckland staff or students to join the meeting automatically:
- Go to your general Zoom settings: https://auckland.zoom.us/profile/setting
- Under Waiting Room options, click Edit Options
- Under Who should go in the Waiting Room, choose Users who are not in your account and not part of your whitelisted domains.
- Then, add *.auckland.zoom.us as a whitelisted domain.
General tips
Avoid sharing Zoom meeting links on public platforms or social media. Instead, send meeting invitations directly to trusted individuals via email or other secure communication channels.
During meetings (if practical), once all the intended participants have joined, lock the meeting to prevent any further entry. This option can be found in the Security button in Zoom.
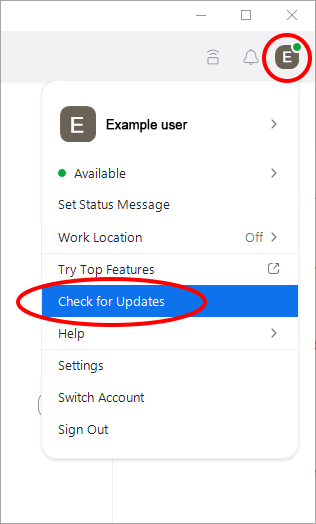
Regularly update your Zoom application to the latest version. New updates often include security enhancements and bug fixes that strengthens your protection against potential vulnerabilities. Do this by checking for updates via the drop-down under your profile picture.
Depending on your meeting requirements, familiarise yourself with Zoom’s security features, such as disabling file transfers, chat functions, or private messaging. We have provided additional instructions on changing your security settings within Zoom.
Avoid clicking on suspicious links or downloading attachments from unverified sources, as they may contain malware or phishing attempts that compromise your security.
It is important to be proactive and implement security measures to reduce the risk of Zoom bombing. In the event of an intrusion, swift action will help mitigate the disruption and restore a secure virtual meeting environment. Prevention is key.
See also
If someone crashes your meeting
Learn about the Zoom settings that help you respond to gatecrashers.
Zoom video conferencing
All the other stuff relating to Zoom.
Page updated 10/04/2025 (page added)